The Largest Platform to Find Cybersecurity Tools
Browse 14,121 the largest platform to find cybersecurity tools
FEATURED
Stay Updated with Mandos Brief
Get strategic cybersecurity insights in your inbox
TRENDING CATEGORIES
FIND ALTERNATIVES TO
View allBROWSE CATEGORIES
View allSecurity operations tools for SIEM, SOAR, threat hunting, incident response, and security operations center (SOC) management.
Professional cybersecurity consulting services including penetration testing, incident response, compliance, and managed security services.
Identity and Access Management solutions for identity governance, access control, authentication, privileged access management, and zero trust security.
GRC tools and platforms for managing cybersecurity governance, risk assessment, compliance monitoring, and regulatory reporting.
Application security tools and solutions for securing web applications, mobile apps, and software throughout the development lifecycle.
Network security tools and solutions for firewalls, intrusion detection, network monitoring, and perimeter security.
Data protection tools and solutions for data encryption, backup, classification, loss prevention, and privacy compliance.
Cloud security tools and solutions for securing cloud infrastructure, containers, serverless applications, and multi-cloud environments.
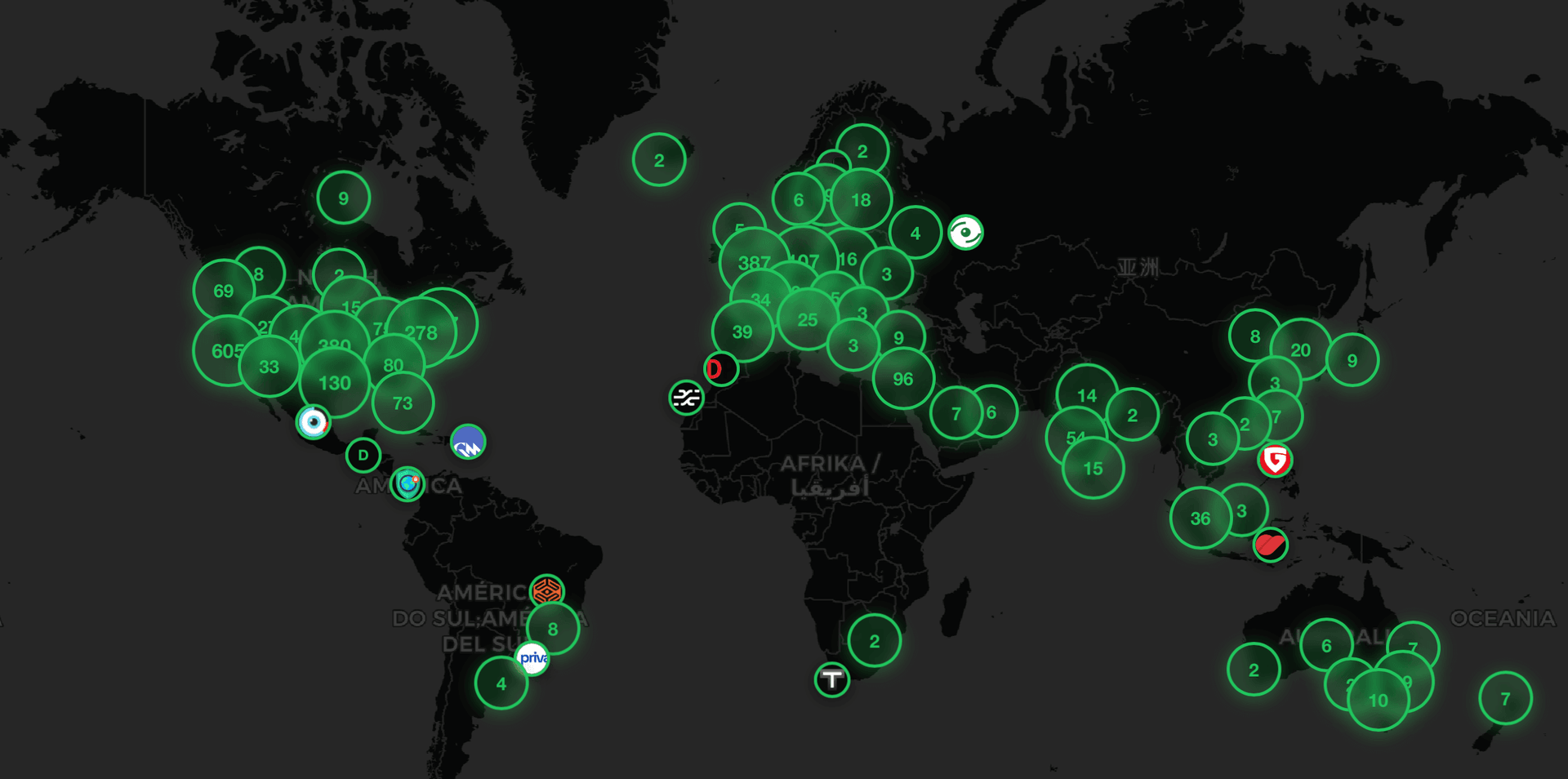
EXPLORE THE CYBERSECURITY MAP
Discover where cybersecurity companies are headquartered. Our interactive map lets you explore the distribution of security vendors across the globe.
Explore the Map